The Invisible Hand of Identity Agents
An agentic use case that actually works. They operate in the background, restoring control of applications where traditional identity systems break.
This article is part of the DTCP Blog series
Most AI pilots are failing. MIT’s Media Lab just put a hard number on it: 95% of enterprise gen‑AI pilots deliver no measurable business return. The problem is not model horsepower. It is weak integration, brittle workflows, and tools that do not fit day‑to‑day operations.
While most enterprises are pursuing flashy demo-friendly AI pilots, the MIT survey highlighted “back office” use cases as having the highest ROI, automating tasks that are administrative, repetitive, and labor‑intensive.
Our view is simple: the AI winners will be startups that master domain-specific context and own the workflows, reliably solving enterprises most brittle bottlenecks. One of the clearest opportunities for agentic software lies in identity. Disconnected apps, uneven controls, and manual tickets block automation and ROI. We will explore the agentic angle in identity and how Cerby is leveraging its position to own the agentic identity workflow - starting from its most painful pain point.
Identity is the right battlefield for agentic software
Identity is upstream of nearly every enterprise workflow. When identity breaks, everything breaks. The problem is simple to describe but painful to fix. The primary cause of these breaks? Disconnected applications.
There is a long tail of such “disconnected” or “nonstandard” apps that do not support SAML, SCIM, OIDC, or clean APIs. These apps sit outside enterprises’ IdP, IGA and PAM. The result is manual provisioning and offboarding, password sprawl, weak or missing MFA, brittle scripts, and audit gaps. With agentic software, this last mile is finally solvable with software, making those apps governable and securable.
The category frame: Agentic Identity
“Agentic Identity” is not a slogan. It is a product requirement. Identity teams need agents that can read and act across UI and API surfaces to enforce policy, close gaps, and write truth back into the system of record. Then they need those agents to keep working when UIs change and vendors move paywalls. That is agentic software applied to identity. This is the next step beyond RPA and it is the one that sticks.
If we believe that application-using agents will be most useful where APIs do not exist, identity’s last mile of disconnected apps is the obvious place to start.
Why a startup wins here
General purpose agents are not going to navigate bespoke enterprise systems or marketing teams’ social stack out of the box. Startups that verticalize agentic software and do the gritty implementation work will define the category.
Cerby’s positioning is direct. Become the agentic identity layer for the applications and identities that the rest of the market cannot touch. Own the workflows, not the widget. That is how you earn long-term data and process control in identity.
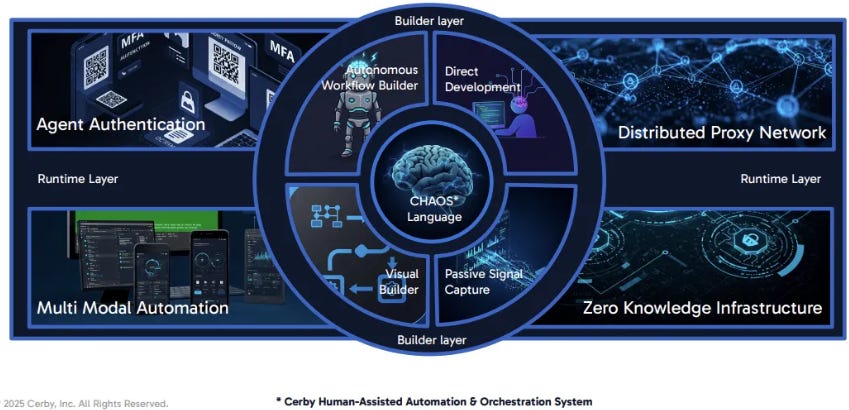
What makes Cerby “agentic”
Cerby is purpose-built to own identity workflows for disconnected apps. It extends the existing stack rather than replacing it.
Here is what that looks like in practice today:
Owning the last mile for any app. Cerby blends API operations with robust UI automation to create programmatic control even when app vendors do not expose one. It learns target workflows through various methods, including the Scout browser extension, and keeps automations healthy with self-healing.
Automating real identity work. One-click add or remove access even without SCIM. Enforce MFA enrollment automatically. Rotate shared and privileged passwords on SCIM or HR events. All of that is enforced for apps that used to be manual.
Snapping into the systems enterprises already run. Cerby easily integrates with Okta, Entra ID, Saviynt and more to bring SSO, lifecycle, group push, access certifications, and governance to apps that previously sat outside the identity perimeter. This is not a sidecar. It is upstream of the workflows.
Scaling through an application network. Thousands of prebuilt, validated integrations and a process to rapidly add new ones when customers need them. This is how to make agentic identity repeatable.
What this means for CISOs and CIOs
You can now stop accepting the attack surface created by disconnected apps.
You do not need to rip and replace your IdP, IGA, or PAM. Cerby extends them to 100% of your app estate.
You can measure the ROI in fewer manual tickets, closed audit findings, and reduced credential risk.
If you are spending teams’ time on joiner/mover/leaver tickets for disconnected apps or paying the “SSO tax” just to get basic security, you are leaving money and risk on the table.
Closing thought
Startups that master context and own workflows will define the first generation of agentic coworkers. In identity, that company is Cerby. If you want to learn more, reach out to us or visit Cerby at booth G-4 at the upcoming Oktane conference in Las Vegas (Sep 24-26th, 2025).
Disclosure: DTCP led Cerby’s Series B in May 2025.